Typo-squatted Online File Converter Tools
The Dangers of Online File Converters
Introduction
In early 2025, the FBI’s Denver Field Office issued an alert warning of a new scam involving fake online file converter tools. These spoofed converter websites mimic legitimate services that convert files (e.g. PDF to Word or MP3 to MP4), but instead they deliver malware to unsuspecting users. The FBI noted that criminals are leveraging the popularity of free file conversion sites to load ransomware and steal data from victims’ computers (fbi.gov). In worst-case scenarios, simply using a phony “free converter” site could lead to a compromised system or even a full-blown ransomware incident (fbi.gov). This emerging threat has gained momentum through 2024-2025, targeting both individual users and organizations searching for quick file format conversions.
How the Fake Converter Scam Works
Spoofed file converter sites appear genuine – they often perform the advertised conversion to avoid raising suspicion (fbi.gov). However, alongside the “converted” file, they embed hidden malware that infects the device. According to the FBI, cybercriminals set up sites claiming to convert or combine files (e.g. DOC to PDF, or merging images into a PDF) and even offer media downloader tools (fbi.gov). The attack flow typically involves:
- Search Engine Ads & Typosquatting: Attackers promote malicious converter sites via paid search ads or misleading URLs. Users searching for “free PDF converter” may click a sponsored result that looks legitimate (webasha.com). The fraudulent sites use minor URL changes to impersonate real services – for example, Imageconvertors[.]com instead of the legitimate “imageconverters.com”, or convertix-api[.]xyz instead of “convertix.com” (webasha.com). Such subtle typos or extra words in the domain name are a red flag for vigilant users.
- Convincing Fake Websites: Once on the site, the user is presented with a polished interface that often copies branding and design from the real service. The victim is invited to upload their file for conversion – a common workflow that builds trust. The site may even show a fake progress bar or CAPTCHA verification to appear more authentic (hackread.com). Behind the scenes, the attacker ensures the service does convert the file (so the user gets a usable output) (fbi.gov), but the output or the process includes a malicious payload.
- Malware Delivery Mechanisms: There are a few ways these scams deliver malware. In some cases, the “converted” file itself is infected – for example, a PDF that hides an exploit or an EXE bundled inside a ZIP (hackread.com). Another tactic is prompting the user to run a tool or command for the conversion. For instance, one campaign tricked users into executing a Windows PowerShell command (under the guise of finishing the PDF conversion) which then downloaded malware (hackread.com). Alternatively, the site might urge users to install a converter software or browser extension – which turns out to be adware or a trojan (malwarebytes.com). In all scenarios, the result is that the victim’s computer gets silently infected once they follow the fake site’s instructions.
- Data Theft and Abuse: Beyond malware installation, the FBI warns that these fake converters can harvest any data the user uploads for conversion (fbi.gov). Sensitive personal or corporate documents provided to a rogue converter could be scraped for personal identifiers, passwords, financial info, or other confidential content (fbi.gov). This means a victim not only risks malware, but also exposure of the information contained in the files they wanted to convert.
In summary, the scam relies on a mix of social engineering and technical trickery: users’ trust in free online tools, convincingly cloned websites, and hidden malware delivery. Next, we’ll examine real-world cases where threat actors impersonated known file converter services to carry out this scheme.
Recent Impersonation Cases of Converter Tools
Threat actors have not limited themselves to just one service – multiple online file conversion tools have been impersonated in recent attacks. Investigations in the past year uncovered sophisticated campaigns in which criminals cloned well-known converter platforms to lure users. Below we detail some notable cases and how to spot their spoofed versions.
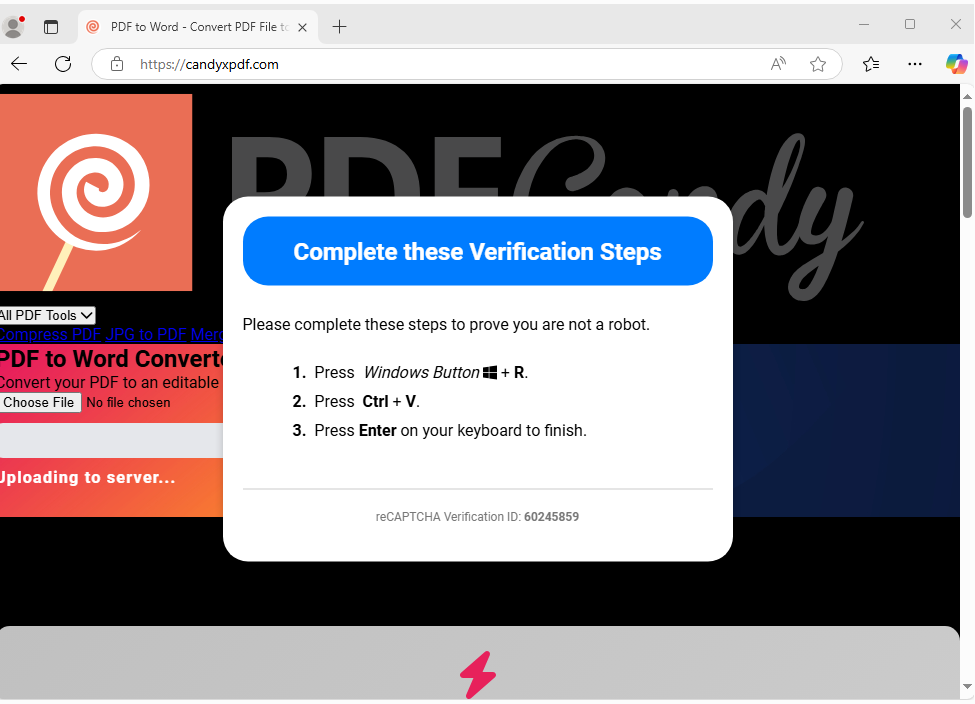
One prominent example is the PDFCandy scam. In April 2025, researchers at CloudSEK reported that attackers were impersonating PDFCandy.com – a popular free PDF conversion service – to distribute malware (hackread.com). The fake sites used domains like “candyxpdf.com” and “candyconverterpdf.com”, which closely resemble the legitimate pdfcandy.com URL (indianexpress.com). The threat actors copied the official PDFCandy branding and user interface “meticulously” to appear authentic (hackread.com). On these look-alike pages, victims were prompted to upload a PDF for conversion, then were unexpectedly presented with a fake CAPTCHA step (hackread.com). This was the pivot to malware delivery: after the CAPTCHA, the site instructed users to run a seemingly innocuous PowerShell command, purportedly to download the converted file (hackread.com). In reality, this executed a chain that fetched a malicious adobe.zip file and ultimately installed ArechClient2 – a powerful information-stealing malware (from the SectopRAT family) – onto the victim’s system (hackread.com). This PDFCandy impersonation campaign was particularly deceptive because the website did convert the PDF as promised while simultaneously infecting the user’s machine. It was also reported that the operators drove traffic to these fake PDFCandy sites via Google Ads, exploiting users searching for PDF converters (hackread.com).
Another case involved an open-source tool called “File Converter”. This is a Windows utility by developer Adrien Allard, whose official website is file-converter.io. In late 2024, users discovered a fraudulent clone site at file-converter.org that claimed to be the same service (github.com). The fake site’s footer even falsely stated it “previously hosted” the open-source project – likely an attempt to legitimize itself (github.com). In reality, the .org site was packaging malware. Downloading the File Converter installer from the imposter domain would infect the system: researchers noted the installer included a hidden dropper that fetched malware in the background (github.com). One user report indicated that the malicious installer was oddly branded with “Zamzar” (a well-known file conversion company), suggesting the attackers used Zamzar’s name to appear trustworthy (github.com). This case highlights a classic typosquatting technique – using a different TLD (.org instead of the real .io domain) to catch users off guard. Anyone who didn’t notice the URL change could easily have mistaken the fake site for the legitimate File Converter project and ended up running malware.
Beyond these specific brands, numerous generic-sounding converter sites have been flagged by security teams. Many don’t impersonate one particular company’s branding, but rather use common keywords to attract search traffic (and thus effectively spoof “a legitimate service” in the eyes of a casual user). For example, a site named Imageconvertors[.]com (note the misspelling of “converters”) was reported as a phishing page distributing malware (webasha.com). Similarly, Convertitoremp3[.]it (Italian for “mp3 converter”), Freejpgtopdfconverter[.]com, and Convertallfiles[.]com are among the malicious domains that have been identified in this trend (webasha.com). Each of these imitates a plausible service name or function. The telltale signs of fraud include odd domain choices (unusual TLDs like .xyz, deliberate misspellings, or extra words like “free” or “pro”), lack of a credible business presence, and sometimes the absence of HTTPS security. Table 1 below summarizes several recent instances of spoofed file converter tools and how to identify them:
| Real Tool / Service | Legitimate Domain | Impersonated Domain(s) | Spoofing Indicators | Reference |
|---|---|---|---|---|
| PDFCandy (online PDF converter) | pdfcandy.com |
candyxpdf.com, candyconverterpdf.com (indianexpress.com) |
Typosquatted look-alike domains (e.g. swapping words); fully cloned website UI and branding (hackread.com); Fake CAPTCHA and unusual download prompts (PowerShell command) | CloudSEK report (hackread.com, hackread.com) |
| File Converter (open-source utility by Adrien Allard) | file-converter.io |
file-converter.org (github.com) |
Domain name squat using different TLD (.org instead of .io); claims to be “previous host” of the project in footer (github.com); Installer is bundled with a malware dropper | GitHub issue report (github.com, github.com) |
| Generic “Free Converter” Sites (multiple) | (various legitimate services) | e.g. Imageconvertors.com (impersonates a generic image converter) (webasha.com), convertix-api.xyz (mimics “Convertix” service) (webasha.com), freejpgtopdfconverter.com, etc. (webasha.com) |
Misspelled or extra words in domain (typosquatting); unusual TLDs (.xyz, .it, etc.); lack of HTTPS or official contact info; often pushed via ads or pop-ups | FBI/Malwarebytes alert (webasha.com, webasha.com) |
Table 1: Notable cases of spoofed file converter tools and how to spot them. Even when the fake sites perform the promised conversion, they carry indicators of fraud such as misleading URLs and unexpected user prompts.
Detecting and Avoiding Spoofed Converter Tools
Given the prevalence of these scams, what can enterprise security teams and vigilant users do to defend against them? Below are recommendations to detect malicious converter sites and avoid falling victim:
- Prefer Trusted Solutions: Where possible, avoid using random online converters altogether (webasha.com). Enterprises should provide approved tools for common file conversions (e.g. Adobe Acrobat for PDFs, Microsoft Office for document format changes (webasha.com)). Cloud storage suites like Google Drive or OneDrive have built-in converters that are far less likely to be malicious (webasha.com). By limiting use of unofficial tools, you eliminate the risk at its source.
- Verify the URL and Security: Always double-check the domain of the service before uploading files. Look for subtle misspellings or extra characters in the URL (for example, “pdfcandy**.co**” vs “pdfcandy.com”). Typosquatted domains are a major warning sign (webasha.com). Ensure the site is using HTTPS (SSL lock icon in the address bar) – while not a guarantee of legitimacy, a lack of HTTPS is a red flag on any site handling file uploads. It’s also wise to search for the service’s reputation or reviews if you’re trying it for the first time (webasha.com). Enterprise security teams can deploy browser extensions or DNS filtering to block known malicious domains and alert users who attempt to visit them.
- Be Wary of Sponsored Search Results: A common infection vector is malicious ads on search engines (webasha.com). Users and IT departments should be cautious with Google/Bing results labeled “Ad” when searching for converters. If you see an ad for a converter service, it’s safer to scroll to a non-sponsored result or navigate to the known official site directly. Using browser ad-blockers can help reduce exposure to these dangerous ads (webasha.com).
- Observe Site Behavior: Even if the site looks legit at first glance, pay attention to any unusual steps in the process. Beware of prompts to download additional software or enter commands – legitimate online converters typically do not require running local executables or scripts. An unexpected CAPTCHA after uploading a file, or being asked to “allow” a download that isn’t the format you expected, should raise suspicion. Enterprise users should be trained to recognize these anomalies and stop when something feels off.
- Leverage Security Tools: Ensure that endpoint protection (antivirus/anti-malware) is active and up to date on all systems (fbi.gov). Modern security software can often detect malicious payloads in downloaded files or block known bad URLs. Additionally, using a reputable browser security extension or DNS security service can block access to phishing and malware sites preemptively (malwarebytes.com). Enterprises might consider network-level defenses that sandbox file downloads – for instance, if a user does download a file from a converter site, it can be automatically scanned or opened in an isolated environment to detect malware before it reaches the user’s device.
- Train and Inform Users: Employee awareness is crucial. IT teams should include the topic of fake online tools (like converters) in security training sessions. Emphasize that just because a Google search finds a tool doesn’t mean it’s safe. Share indicators of spoofed sites (strange URLs, etc.) and encourage staff to report anything suspicious. The FBI alert itself stressed that education is the best way to thwart these fraudsters before users fall victim (fbi.gov).
- Incident Response Preparedness: In an enterprise setting, be prepared in case a user does accidentally engage with a spoofed converter. Have clear steps for them to report the incident. Immediately scan the affected machine for malware and check if any credentials may have been stolen (since info-stealers target browser passwords, etc.). The FBI and security experts advise victims to change all passwords (from a clean device) and notify financial institutions if any sensitive data might have been exposed (fbi.gov). Fast response can contain damage if malware is discovered early.
By following these practices, organizations and users can dramatically reduce the risk posed by fake file converter services. Diligence in verifying online tools, network safeguards, and user education are key to defending against this evolving threat. As always, if an online offer seems too convenient or comes from an unverified source, it should be treated with caution. The trend of spoofed online file converters underscores a classic cybersecurity lesson: even routine tasks (like converting a document) can become dangerous when trust is misplaced. Stay alert and stick to known, reputable services to keep your files – and systems – safe (webasha.com).
